Beast trojan download - BEAST 1.10.4 freeware download - Designed to help you with the Bayesian MCMC analysis - Freeware downloads - best freeware - Best Freeware Download. Michael Jordan (Original Mix) - Carnage, Tony JuniorSound RecordingOwned byBelieve MusicWMGSMEIn the name of: Netswork Records. Then, download and install this free protection software Trojan Remover 2019 full version in order to remove the Trojan contents and to improve the performance of your computer. This best virus protection software is offering a 30-days free trial so that you can utilize the features of a full version free for 30-days. BEAST 2 includes a graphical user-interface for setting up standard analyses and a suit of programs for analysing the results. Download The latest version of BEAST 2 is version 2.5.1:. Download for Windows /. Download for Mac OS X /. Download for Linux / If you download a version of BEAST without Java, you need to install Java separately. Aug 03, 2004 The Beast 2.07 has been released on August 03, 2004. Beast is a powerful Remote Administration Tool (AKA trojan) built with Delphi. One of the distinct features of the Beast is that is an all-in-one trojan (client, server, server editor, plugins are stored in the same application). Besides, a binder is implemented in the Beast main application.
Make text messages secret by hiding them within images with password protection, and easily decrypt the files using this application
Trojan is a very simple-to-use software utility that gives you the possibility to make messages secret by embedding them within images.
They are password protected, so you will need the right key to decrypt them. The tool offers support for image files with the .bmp, .jpg, .jpeg, ,gif, .mng, .png, .pcs, .tif and .tga extensions.
Free Anti Trojan Download

Simple setup and GUI
After a rapid and uneventful setup operation, Trojan shows a large window with an outdated look and neatly organized structure, showing all options available. You can start by indicating an image file from the computer that you can preview in the main frame.
Encrypt and decrypt photos easily
In the bottom part of the screen you can write or paste your secret message, after which you can enter a password to decrypt it. In the following step, all you have to do is save the new encrypted image to file by establishing its name, destination and format (only .bmp, .png and .tif are supported for the output). Only Trojan is capable of decrypting images with the help of the correct password, so make sure not to lose it.
Evaluation and conclusion
As expected, the tool didn't put a strain on the overall performance of the computer during our testing, thanks to the fact that it needed low CPU and memory to work properly. It had a good response time, encrypted and decrypted files swiftly, and didn't hang, crash or show error notifications.

Although it doesn't integrate sophisticated features, Trojan does its job quite well, providing you with a simple and fast method for encrypting text within photos using a password.

Filed under
Download Hubs
Trojan is part of these download collections: Steganography Tools
Trojan
was reviewed by
Elena OprisVirus Download
2.5/5
This enables Disqus, Inc. to process some of your data. Disqus privacy policyTrojan 1.0
add to watchlistsend us an update- runs on:
- Windows All
- file size:
- 658 KB
- filename:
- Trojan.zip
- main category:
- Security
- developer:
- visit homepage
top alternatives FREE
top alternatives PAID
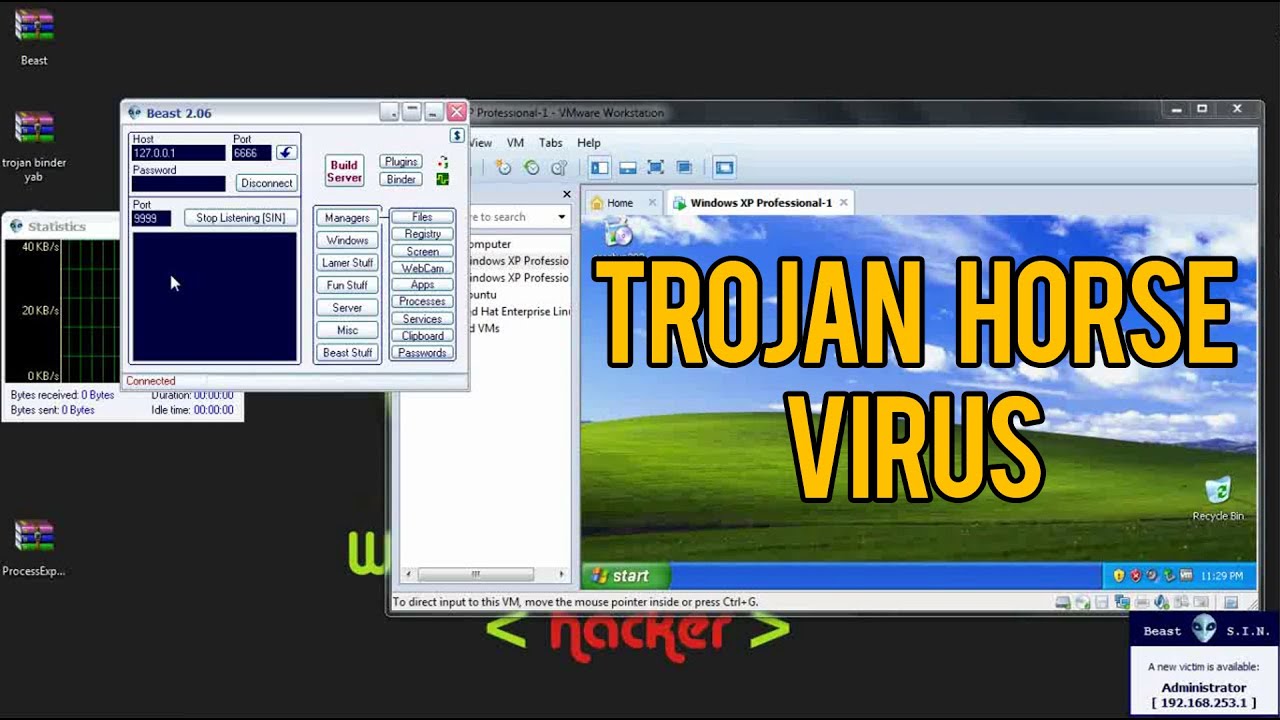
Beast 2.07Introduction:
The Beast 2.07 has been released on August 03, 2004. Beast is a powerful Remote Administration Tool (AKA Trojan built with Delphi. One of the distinct features of the Beast is that is an all-in-one Trojan (client, server, server editor, plugins are stored in the same application). Besides, a binder is implemented in the Beast main application. Beast 2.07 is a complete Trojan being available 2 types of connection: reverse and direct. The default settings are with direct connection. The older Beasts (2.02 etc.) were using direct connection, i.e.the server opens a port and waits for connections from the client. The reverse connection (feature available since 2.05 version) means that the client is waiting for connections, using S.I.N. (Static IP Notification), from the on-line servers. That method has many advantages, the main being that Beast can be used with servers behind routers or in LAN's The server can be extracted from the Beast and its size is only 30 KB (compressed) if aren't used the injecting technologies. If you choose a server which will be injected in Explorer.exe, Internet Explorer or another application, its size will be 49 KB (compressed), even so being small enough. Considering the multitude of tasks which can be performed by the server, the size is excellent. Beast 2.07 has a built-in plugin system, being available 4 plugins for the most size consuming tasks like the Screen Manager and Passwords (Protected Storage, ICQ/Trillian, Dial-up) As you might know from the previous versions, an important feature of the server is that is using the injecting technology. At the first run the server is injecting in the memory of Explorer.exe (on 9x systems in systray.exe). Afterwards, from Explorer.exe are performing injections in the other hosts (in the case the server isn't built for Explorer.exe injection), according with the options you chose when building the server. The main benefits of this type of running is that from Explorer.exe are monitoring the other injected applications and, by example, if the Internet Explorer is closed, from Explorer.exe will be started again and injected with the dll. If the server in injected in Explorer.exe it won't be visible on any Task Manager, so that could be a good option.When the server is injected in Internet Explorer, the server will be visible in Task Manager, but inthis way the firewalls could be more easily by-passed. And is not a big deal if it is visible in TaskMgr because in the case when the IE process is closed will be automatically run again ;) The server stability is almost 100%, the server can't be crashed by closing the client during a file transfer or other operations). Usually the server (dll) is residing in the windows/system directory.With Beast 2.07 for the server aren't needed the administrator privileges on NT (2k, XP), the server can run on a restricted user (guest etc.) account, in this case being located under <Documents and Settings> directory
Well, it's a remote administration tool and some people say it's a Trojan ;) With Beast you can control remote computers and also spy them...
2) Is it legal? Sure it is, if it's used on your private network and you don't make any harm to other people.
3) How to start? First you have to build a server, (See chapter 3 server settings), then you have to manage to install the server on a remote machine and afterwards you'll be able to control that machine.
4) How can I find the IP and password for connection? When you build the server you have to configure at least one notification method, so whenever the remote machine is on the beast server runs.
5) Why can't I connect? Well, could be few reasons: the connection could be blocked by a firewall, the remote computer is in a LAN or behinf a proxy and you configured the server with direct connection, or the computer is offline etc.
6) Oh, I infected myself, what can I do? The easiest way to uninstall the server is to connect to yourself (at address 127.0.0.1) and click the Kill Server button.
7) Can you send me the source code? I'm a student and I don't have money, all I want is to learn how to code. LOL, no.
Complete Detailed Tutorial Download HTML File Below... |
|




 was reviewed by Elena Opris
was reviewed by Elena Opris